From my client (which is Windows Server 2008 R2), tried accessing URL: works. Also, tried URL: works. NOTE: we are still not sure if it's using TLS 1.0. Now, to force RDWeb to work on TLS only: Open Regedit; Go to HKEYLOCALMACHINE SYSTEM CurrentControlSet Control Terminal Server WinStations RDP-Tcp. TLS 1.1 and TLS 1.2 in Windows Server 2008 SP2. The server is restarted, and we have also enabled the TLS 1.1 and TLS 1.2 in registry and restarted the server. But when we use IISCrypto.exe to check the setting, it still does not show TLS 1.1 as well as TLS 1.2. When we go to IE Internet Options Advanced, we also still cannot see 'Use TLS 1.1' and 'Use TLS 1.2'. Please advice. Mar 16, 2018 I have more than 400 servers all are windows servers(2008,2012),In which i need to check TLS 1.2 is enabled or not. Where i have to check about TLS 1.2 is enabled or not? And please letme know have any script to get the output in excel. I know we can check via regedit from the below path and need script to check for 400 servers. Jul 20, 2017 This post is authored by Arden White, Senior Program Manager, Windows Servicing and Delivery. As a follow-up to our announcement regarding TLS 1.2 support at Microsoft we are announcing that support for TLS1.1/TLS 1.2 on Windows Server 2008 is now available for download as of July 18th, 2017. We’re offering this support in recognition that. Feb 21, 2018 This update provides support for Transport Layer Security (TLS) 1.1 and TLS 1.2 in Windows Server 2008 Service Pack 2 (SP2) for Remote Desktop Services (RDS). For more information about how to enable or disable TLS, see the TLS/SSL Settings. Applies to: Windows Server 2008 Service Pack 2. This update provides support for Transport Layer Security (TLS) 1.1 and TLS 1.2 in Windows Server 2008 Service Pack 2 (SP2) for Remote Desktop Services (RDS). For more information about how to enable or disable TLS, see the TLS/SSL Settings.
This post is authored by Arden White, Senior Program Manager, Windows Servicing and Delivery.
How to Disable TLS on a Windows 2008 Server. On W2K8 R2 SP1 servers and higher, support for TLS 1.1 and TLS 1.2 are supported. Disable TLS 1.0: - Enable TLS 1.2: HKEYLOCALMACHINE SYSTEM CurrentControlSet Control SecurityProviders SCHANNEL Protocols TLS 1.2 - Reboot the server to pick up the changes.
As a follow-up to our announcement regarding TLS 1.2 support at Microsoft we are announcing that support for TLS1.1/TLS 1.2 on Windows Server 2008 is now available for download as of July 18th, 2017. We’re offering this support in recognition that our customers have a strong demand for support for these newer protocols in their environment and in recognition of the extended lifetime of Windows Server 2008 under the Windows Server Premium Assurance offering.
This update for Windows Server 2008 will include support for both TLS 1.1 and TLS 1.2. For application compatibility purposes, these protocols will be disabled by default in a manner similar to the TLS 1.1/TLS 1.2 support that was disabled by default in Windows 7 and Windows Server 2008 R2. After downloading and installing the update these protocols can be enabled by setting the registry keys described in KB4019276.
This update is being made available on the following timeline:
| Release Date | Channels | Classification |
| July 18, 2017 | Microsoft Catalog | |
| August 15, 2017 | Windows Update/WSUS/Catalog | Optional |
| September 12, 2017 | Windows Update/WSUS/Catalog | Recommended |
I have a 2008 DC and a 2008 AD CS server and a Windows 7 client. What I would like is to require the certificate to be used when RDPing to the server.
The certificate is valid, and if I connect using the FQDN I am shown that i was authenticated by both the certificate and Kerberos as expected. When I connect with just the hostname I am allowed to connect and am only authenticated by Kerberos, even though I have Require TLS 1.0 set on the server that I am RDPing to. I fully understand that the certificate will not be valid unless the server is accessed by FQDN, what I want to do is disallow connections that do not use the certificate AND Kerberos.
I thought that setting Require TLS 1.0 would do it. What am I missing?
MDMarraMDMarraWindows Server 2008 R2 Rdp Tls 1.2
3 Answers
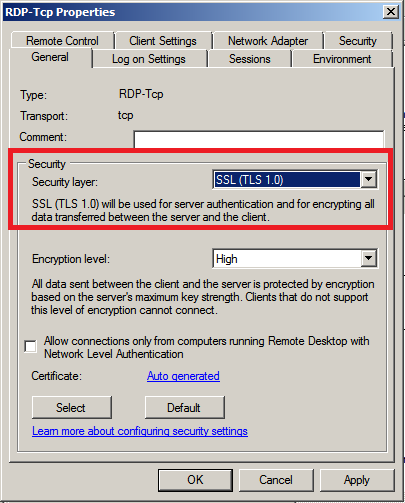
- Start -> Administrative Tools -> Terminal Services -> Terminal Services Configuration
- Right click RDP-Tcp and choose Properties
- 'Security Layer' defaults to 'Negotiate' and must be changed to 'SSL (TLS 1.0)'
- 'Encryption Level' must be set to 'High' or 'FIPS Compliant'
Reference: http://technet.microsoft.com/en-us/library/cc782610(WS.10).aspx
edit:The Microsoft Technet article indicates that TLS cannot be enabled via Group Policy. However, I have done some experimentation with Process Monitor and Regedit and have determined that you can change these settings by setting the appropriate registry values, as follows.
To set Minimum Encryption Level to 'High' instead of 'Client Compatible':
HKLMSystemCurrentControlSetControlTerminal ServerWinStationsRDP-TcpMinEncryptionLevel REG_DWORD Value: 3
To set Security Layer to 'SSL (TLS 1.0)' instead of 'Negotiate':
HKLMSystemCurrentControlSetControlTerminal ServerWinStationsRDP-TcpSecurityLayer
REG_DWORD Value: 2
To test your scenario, here is what I did:
- I have Windows Server 2008 R2 DC
- Installed Roles -> Active Directory Certificate Services, Active Directory Domain Services,
Remote Desktop Services -> Remote Desktop Web Access, Web Server (IIS). Since this is my only DC, I have DNS Server and DHCP Server installed as well - Installed
Server Authentication Certificateon my IIS Web site, it also hosts RDWeb application - Change Authentication on
RDWeb from Anonymous to Windows Authentication - accessed the Web site from the server itself, URL: https://localhost/rdweb. Works fine
- From my client (which is Windows Server 2008 R2), tried accessing URL: https://fqdn/rdweb works. Also, tried URL: https://server_name/rdweb.. works.
NOTE: we are still not sure if it's using TLS 1.0
Now, to force RDWeb to work on TLS only:
- Open Regedit
- Go to
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp - Create a new
Binary Valueand name itSSLCertificateSHA1Hash - Copy the thumbprint from the SSL Certificate and add it as the value of SSLCertificateSHA1Hash
e.g.:
Now, accessed the website URL: https://fqdn/rdweb while tracing it using fiddler, we see all HTTPS connection with Cipher: 0x2F. Tried using the URL: https://server_name the same result.
According to http://tools.ietf.org/html/rfc5289,CipherSuite TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 = {0xC0,0x2F};
Also, check this RDP with custom certificate in Windows 7? (No tsconfig.msc or Group Policy setting)
For WMI, you can check the article Win32_TSGeneralSetting Class
Vivek KumbharVivek KumbharHave you confirmed with a packet capture that the client is not negotiating a TLS connection? That is the only way I know to definitively verify it is working as expected.
Greg Askew